View Authentication settings
To open the authentication settings for your project’s database, follow these steps:.png?fit=max&auto=format&n=Akhg1ig10vOZu5es&q=85&s=e1dfd1a6f283677b6354adc711a3b5d7)
- Log in to your Bolt project.
- Click the database icon in the top center of your screen.
- Click Authentication in the left menu.
Email authentication
This option allows your project’s users to sign up using their email address. Clicking Email in the Authentication settings opens the Email Provider Settings window, where you can enable or disable the following options:- Allow or block email-based signup and login
- Require users to confirm their email after signing up
- Require confirmation from the old address before changing an email
- Require recent login (reauthentication) before changing a password
- Prevent signups with weak or commonly used passwords
Edit email templates
Bolt lets you edit the email templates used to communicate with users. To edit your templates, follow these steps:- Click the database icon in the top center of your screen.
- Click Authentication.
- Click the Email row.
- Click Edit email templates.
- Choose the template you want to edit from the top menu.
- Change the subject line or message body as needed.
Reset email templates to default
If you have updated your email templates and want to return to the original versions, click reset all templates to their default. This link appears in blue at the bottom of the editing window.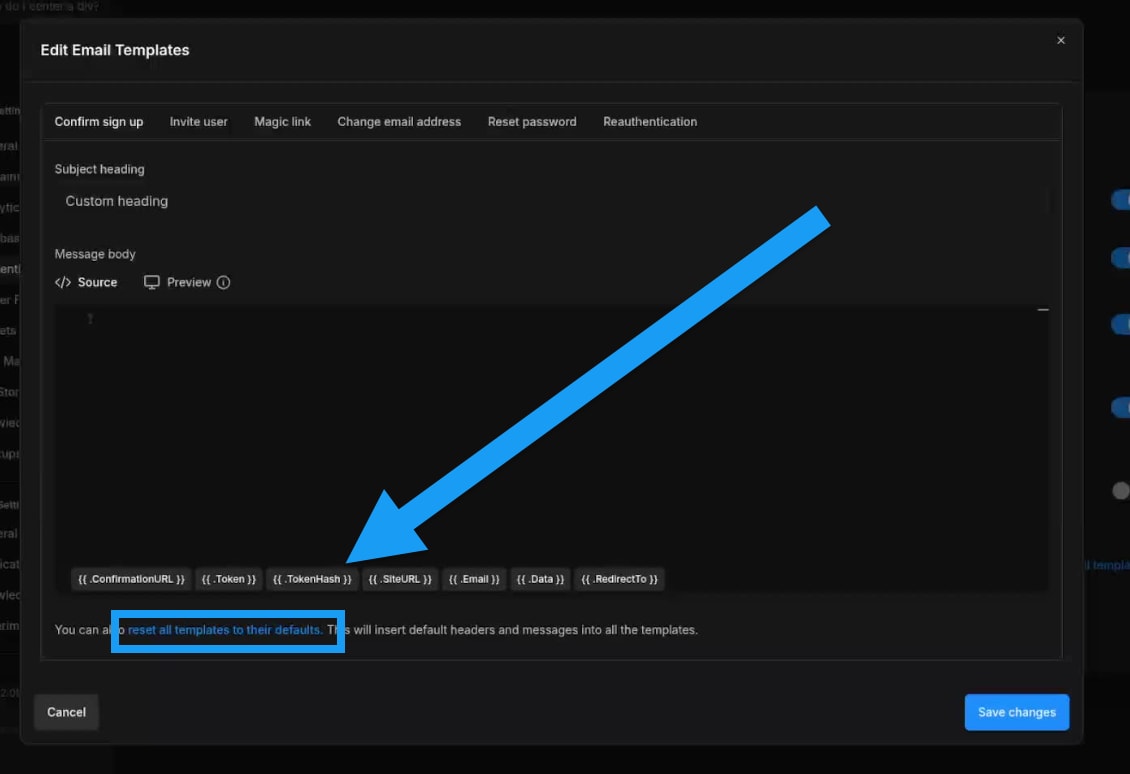
Email template terminology
The templating system provides the following variables for use:| Name | Description |
|---|---|
{{ .ConfirmationURL }} | Contains the confirmation URL. For example, a signup confirmation URL would look like: https://project-ref.bolt.host/auth/v1/verify?token={{ .TokenHash }}&type=email&redirect_to=https://example.com/path . |
{{ .Token }} | Contains a 6-digit One-Time-Password (OTP) that can be used instead of the {{. ConfirmationURL }} . |
{{ .TokenHash }} | Contains a hashed version of the {{ .Token }}. This is useful for constructing your own email link in the email template. |
{{ .SiteURL }} | Contains your application’s Site URL. This can be configured in your project’s authentication settings. |
{{ .RedirectTo }} | Contains the redirect URL passed when signUp, signInWithOtp, signInWithOAuth, resetPasswordForEmail or inviteUserByEmail is called. The redirect URL allow list can be configured in your project’s authentication settings. |
{{ .Data }} | Contains metadata from auth.users.user_metadata. Use this to personalize the email message. |
{{ .Email }} | Contains the original email address of the user. Empty when trying to link an email address to an anonymous user. |
{{ .NewEmail }} | Contains the new email address of the user. This variable is only supported in the “Change Email Address” template. |
Bolt Database email templates are powered by Supabase technology. If you want a deeper look at topics like mobile deep linking, email prefetching, routing signups through a server endpoint, or tailoring emails based on signup method, see the Supabase Email Templates documentation.
Google authentication
This option allows your project’s users to sign up using Google Secure Sign-On (SSO), meaning they can log in with their Google accounts instead of signing up with an email and password.For a full Google SSO setup guide, see Google SSO authentication.
- Allow or block Google sign-in
- Enter your Google Client ID
- Enter your Google OAuth Client Secret
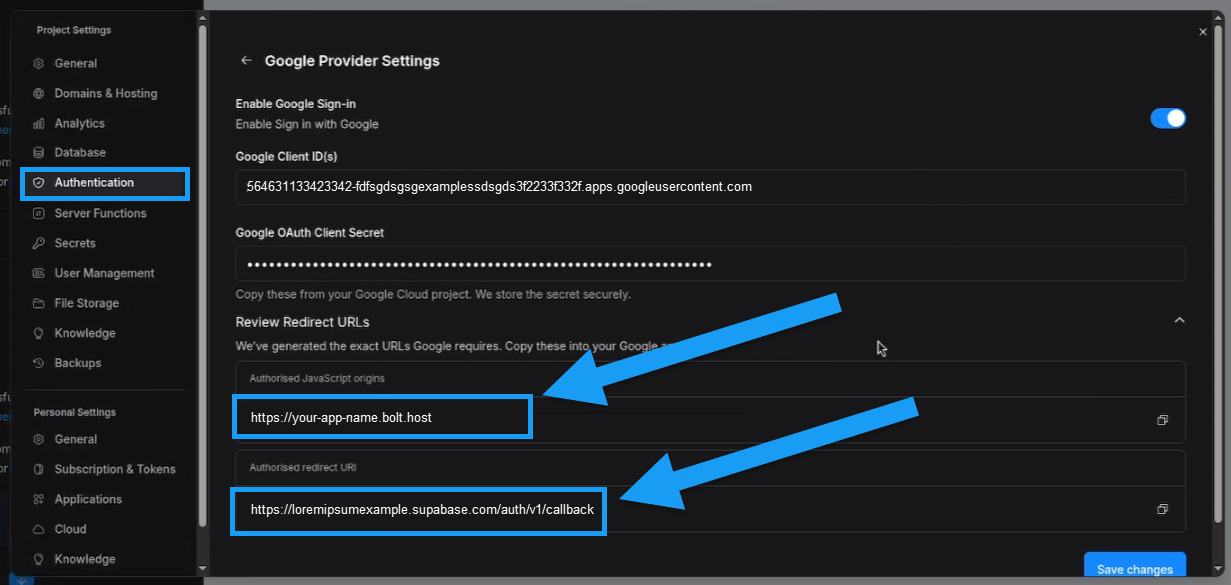
Advanced Authentication options
https://bolt-native-database-ocg0.bolt.host/**
Automatic updates
You don’t need to manage these URLs manually in most cases. Bolt will automatically update these values when needed.
If you need to override these values, you can. Bolt will respect your manual changes.
Set up a reset password flow in your application
Bolt Database and Supabase include built-in password reset functionality. To use it in your application, you need to ask Bolt to add it for you.Requesting reset password support
If your app already has a login screen that uses Supabase or Bolt Database authentication, you can enable password reset by sending Bolt a short instruction. For example:Add reset password functionality to my project.Add a forgot password button to the login screen.
How the password reset link works
The reset email contains a link that sends the user back to your application and automatically authenticates them. Where that link sends the user depends on your authentication settings. Supabase only redirects users to URLs that are included in the URI Allow List. If the original URL is not listed there, Supabase falls back to the Site URL. By default, Bolt projects uselocalhost:3000 as the Site URL. This does not work for live applications.
When you publish a project, Bolt usually updates these settings automatically. In some cases, you may need to edit them manually, especially if your app uses multiple domains.
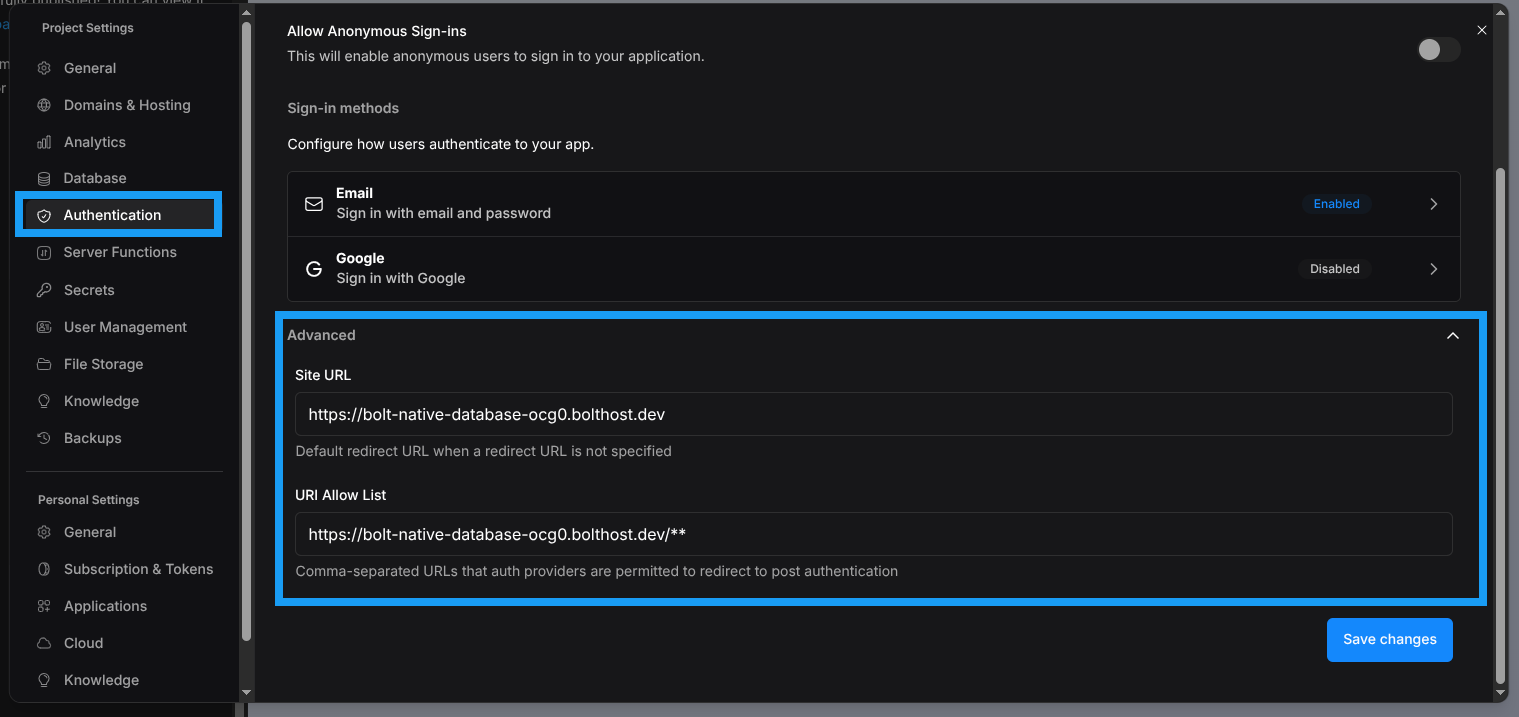
What to check in authentication settings
Make sure the following are set correctly in your authentication settings:- Site URL
This should be the primary live URL of your app. - URI Allow List
Add all domains and paths that users may return to after authentication, including any reset password routes.
Redirecting users to a reset password screen
By default, users who click the reset link may land on the main dashboard instead of a reset password screen. To avoid this, you can give Bolt more specific instructions. Here is an example prompt you can use:Add reset password functionality. There should be a ‘Forgot password’ button on the login screen that sends a reset password email. When the user clicks the link in the email, it includes #type=recovery in the URL. Use this to redirect the authenticated user to a /reset-password screen.
This ensures users land on the correct screen and can set a new password smoothly.